This is your very first post. Click the Edit link to modify or delete it, or start a new post. If you like, use this post to tell readers why you started this blog and what you plan to do with it.

Another hacker attack: letters from the “SBU Academy”
Another hacker attack: letters from the “SBU Academy”
The government computer emergency response team of Ukraine CERT-UA, which operates under the State Special Communications, reports on the mass distribution of dangerous e-mails with the topics “Information Bulletin” and “Combat Order”. They are sent to private e-mail addresses, in particular, supposedly from the National Academy of the Security Service of Ukraine,” the message reads.
According to cyber experts, opening the attachments contained in the emails will lead to the launch of the GammaLoad.PS1_v2 malware on the computer.
The attack is linked to the UAC-0010 (Armageddon) group. This Russian FSB hacker group is one of those that have been actively attacking the critical information infrastructure of Ukraine since the beginning of the full-scale military invasion of Russia.
The State Intelligence Service notes that cybercriminals usually use topics that are painful for Ukrainians. For example, during a similar attack in May, members of Armageddon speculated on the subject of occupied Kherson
Pentesting
CybersecurityAwareness
Cyberian
All you need to know
This how to learn..






What you need to know

How to make email reply automatically




Here this information 188 application banned by govt







August 29, 2020 cyberian

Emotet, a notorious email-based malware behind several botnet-driven spam campaigns and ransomware attacks, contained a flaw that allowed cybersecurity researchers to activate a kill-switch and prevent the malware from infecting systems for six months.
“Most of the vulnerabilities and exploits that you read about are good news for attackers and bad news for the rest of us,” Binary Defense’s James Quinn said.
“However, it’s important to keep in mind that malware is software that can also have flaws. Just as attackers can exploit flaws in legitimate software to cause harm, defenders can also reverse-engineer malware to discover its vulnerabilities and then exploit those to defeat the malware.”
The kill-switch was alive between February 6, 2020, to August 6, 2020, for 182 days, before the malware authors patched their malware and closed the vulnerability.

Since its first identification in 2014, Emotet has evolved from its initial roots as a banking malware to a “Swiss Army knife” that can serve as a downloader, information stealer, and spambot depending on how it’s deployed.
Early this February, it developed a new feature to leverage already infected devices to identify and compromise fresh victims connected to nearby Wi-Fi networks.
Along with this feature update came a new persistence mechanism, according to Binary Defense, which “generated a filename to save the malware on each victim system, using a randomly chosen exe or dll system filename from the system32 directory.”
The change in itself was straight-forward: it encrypted the filename with an XOR key that was then saved to the Windows registry value set to the victim’s volume serial number.
The first version of the kill-switch developed by Binary Defense, which went live about 37 hours after Emotet unveiled the above changes, employed a PowerShell script that would generate the registry key value for each victim and set the data for each value to null.
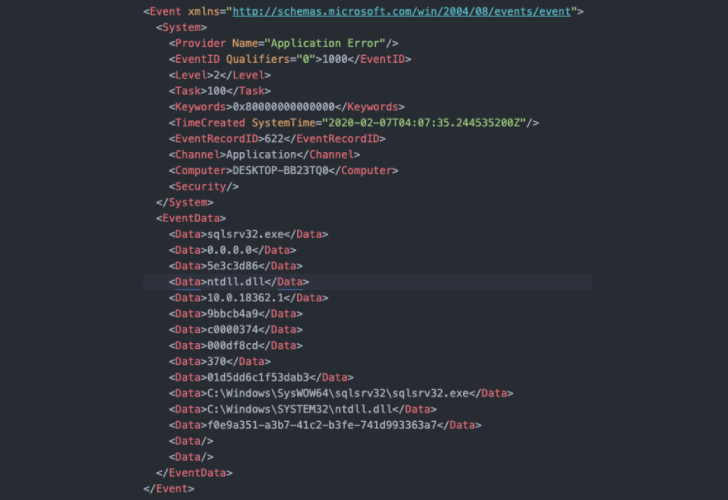
This way, when the malware checked the registry for the filename, it would end up loading an empty exe “.exe,” thus stopping the malware from running on the target system.
“When the malware attempts to execute ‘.exe,’ it would be unable to run because ‘.’ translates to the current working directory for many operating systems,” Quinn noted.
EmoCrash to Thwart Emotet
That’s not all. In an improvised version of the kill-switch, called EmoCrash, Quinn said he was able to exploit a buffer overflow vulnerability discovered in the malware’s installation routine to crash Emotet during the installation process, thereby effectively preventing users from getting infected.
https://42097f8b2e7fd5fdfcb860cd38dd5a40.safeframe.googlesyndication.com/safeframe/1-0-37/html/container.html
So instead of resetting the registry value, the script works by identifying the system architecture to generate the install registry value for the user’s volume serial number, using it to save a buffer of 832 bytes.
“This tiny data buffer was all that was needed to crash Emotet, and could even be deployed prior to infection (like a vaccine) or mid-infection (like a killswitch),” Quinn said. “Two crash logs would appear with event ID 1000 and 1001, which could be used to identify endpoints with disabled and dead Emotet binaries after deployment of the killswitch (and a computer restart).”
To keep it a secret from threat actors and patch their code, Binary Defense said it coordinated with Computer Emergency Response Teams (CERTs) and Team Cymru to distribute the EmoCrash exploit script to susceptible organizations.
Although Emotet retired its registry key-based installation method in mid-April, it wasn’t until August 6 when an update to the malware loader entirely removed the vulnerable registry value code.
“On August 29 2020, Emotet finally returned to spamming after their several months-long development period,” Quinn said. “With EmoCrash still active at the start of their full return, up until August 6, EmoCrash was able to provide total protection from Emotet.”
“Not bad for a 832-byte buffer!,” he added.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.ShareShareCommentsSHARE

Cybersecurity Newsletter
Sign up for cybersecurity newsletter and get latest news updates delivered straight to your inbox daily.EmailLatest StoriesIranian Hackers Pose as Journalists to Trick Victi…QakBot Banking Trojan Returned With New Sneaky Tri…Russian Arrested After Offering $1 Million to U.S….APT Hackers Exploit Autodesk 3ds Max Software for …Other StoriesWebinar — Secure Code Warrior: Dev to DevSecLearn Secure Coding with Secure Code WarriorHow Hackers Spy on Phone CallsFlaws in Intel, ARM, IBM, AMD ProcessorsOnline Courses and SoftwareEthical Hacking – Practical Training1000+ Premium Online CoursesCybersecurity Certification TrainingCompTIA IT Certification TrainingFollow UsAbout
Pages
RSS Feeds Contact Us Telegram Channel© The Hacker News, 2019. All Rights Reserved.
Learn the skill today
Are you very much interested in Learning cyber security … Here is a group that I have made available for anyone who has interest in learning
Beginner class for cyber security
Security
Cloud Computing
AWS
GCP
Sysadmin
Linux
WebSphere
Tomcat
WordPress
Joomla
Startup
Career
Performance
Apache HTTP
Nginx
Cloudflare
SEO
Hosting
Design
Chatbot
Type your search query and hit enter:
Type Here
All Rights Reserved
Geekflare
Type your search query and hit enter:
Type Here
HOMEPAGESECURITY
SECURITY
An Introduction to Cyber Security Basics for Beginner
The basics of cybersecurity
Cybersecurity is the most concerned matter as cyber threats and attacks are overgrowing.
Attackers are now using more sophisticated techniques to target the systems. Individuals, small-scale businesses or large organization, are all being impacted. So, all these firms whether IT or non-IT firms have understood the importance of Cyber Security and focusing on adopting all possible measures to deal with cyber threats.
With the game up for cyber threats and hackers, organizations and their employees should take a step head to deal with them. As we like to connect everything to the internet, this also increases the chances of vulnerabilities, breaches, and flaws.
Gone are the days when passwords were enough to protect the system and its data. We all want to protect our personal and professional data, and thus Cyber Security is what you should know to ensure data protection.
So, lets being with defining the term Cyber Security….
What is Cyber Security?
Cyber Security is the process and techniques involved in protecting sensitive data, computer systems, networks and software applications from cyber attacks. The cyber attacks are general terminology which covers a large number of topics, but some of the popular are:
Tampering systems and data stored within
Exploitation of resources
Unauthorized access to the targeted system and accessing sensitive information
Disrupting normal functioning of the business and its processes
Using ransomware attacks to encrypt data and extort money from victims
The attacks are now becoming more innovative and sophisticated that is capable of disrupting the security and hacking the systems. So it’s very challenging for every business and security analyst to overcome this challenge and fight back with these attacks.
To understand the need for Cyber Security measures and its practices, let’s have a quick look at the types of threats and attacks.
Ransomware
Ransomware is a file encryption software program that uses a unique robust encryption algorithm to encrypt the files on the target system.
The authors of the Ransomware threat generate a unique decryption key for each of its victims and save it in a remote server. Thus, users cannot access their files by any application.
The ransomware authors take advantage of this and demand a considerable ransom amount from the victims to provide the decryption code or decrypt the data. But such attacks have any guarantee of recovery of data even after paying the ransom.
Botnets Attacks
Botnets was initially designed to carry out a specific tasks within a group.
It is defined as a network or group of devices connected with the same network to execute a task. But this is now being used by bad actors and hackers that attempts to access the network and inject any malicious code or malware to disrupt its working. Some of the botnet attacks include:
Distributed Denial of Service (DDoS) attacks
Spreading spam emails
Stealing of confidential data
Botnets attacks are generally carried out against large-scale businesses and organization due to its huge data access. Through this attack, the hackers can control a large number of devices and compromise them for its evil motives.
Social Engineering Attacks
Social engineering are now a common tactics used by cyber criminals to gather user’s sensitive information.
It may trick you by displaying attractive advertisements, prizes, huge offers and so and ask you to feed your personal and bank account details. All the information you enter there is cloned and used for financial frauds, identity frauds and so.
It is worth saying about the ZEUS virus that is active since 2007 and is being used as a social engineering attack methods to steal banking details of the victims. Along with financial losses, Social engineering attacks are capable of downloading other destructive threats to the concerned system.
Cryptocurrency Hijacking
Cryptocurrency hijacking is the new addition to this cyber world.
As the digital currency and mining are becoming popular, so it is among cyber criminals. They have found their evil benefit to the crypto-currency mining which involves complex computing to mine virtual currency like Bitcoin, Ethereum, Monero, Litecoin so on.
Cryptocurrency investors and traders are the soft target for this attack.
Cryptocurrency hijacking also known as “Cryptojacking”. It is a program designed to inject mining codes silently to the system. Thus the hacker silently uses the CPU, GPU and power resources of the attacked system to mine for the cryptocurrency.
The technique is used to particularly mine Monero coins. As the mining is a complex process, it consumes most of the CPU resources which impacts the system’s performance. Also, it is done under all your expenses, so the victim may get ha huge electricity bill and internet bill.
It also lessens the lifespan of the affected device.
Phishing
Phishing is a fraudulent action of sending spam emails by imitating to be from any legitimate source.
Such mails have a strong subject line with attachments like an invoice, job offers, big offers from reputable shipping services or any important mail from higher officials of the company.
The phishing scam attacks are the most common cyber attacks that aims to steal sensitive data. Like Login credentials, credit card numbers, bank account information and so on. To avoid this, you should learn more about phishing email campaigns and its preventive measures. One can also use email filtering technologies to avoid this attack.
Along with these, 2019 will seek the potential in biometric attacks, AI attacks and IoT attacks. Many companies and organizations are witnessing large-scale cyber attacks and there is no stop for them. Despite the constant security analysis and updates, the rise of cyber-threat is consistent. Thus, it is worth to educate yourself with the basics of cybersecurity and its implementations.
The key concept of Cyber Security?
The Cyber Security on a whole is a very broad term but is based on three fundamental concepts known as “The CIA Triad“.
It consists of Confidentiality, Integrity and Availability. This model is designed to guide the organization with the policies of Cyber Security in the realm of Information security.
The Basics of CyberSecurity
Confidentiality
It defines the rules that limits the access of information. Confidentiality takes on the measures to restrict the sensitive information from being accessed by cyber attackers and hackers.
In an organization, peoples are allowed or denied the access of information according to its category by authorizing the right persons in a department. They are also given proper training about the sharing of information and securing their accounts with strong passwords.
They can change the way data is handled within an organization to ensure data protection. Various ways to ensure confidentiality, like: two-factor authentication, Data encryption, data classification, biometric verification, and security tokens.
Integrity
This assures that the data is consistent, accurate and trustworthy over its time period. It means that the data within the transit should not be changed, altered, deleted or illegally being accessed.
Proper measures should be taken in an organization to ensure its safety. File permissions and user access control are the measures controlling the data breach. Also, there should be tools and technologies implemented to detect any change or breach in the data. Various Organizations uses a checksum, and even cryptographic checksum to verify the integrity of data.
To cope with data loss or accidental deletion or even cyber attacks, regular backups should be there. Cloud backups are now the most trusted solution for this.
Availability
Availability in terms of all necessary components like hardware, software, networks, devices and security equipment should all be maintained and upgraded. This will ensure the smooth functioning and access of Data without any disruption. Also providing constant communication between the components through providing enough bandwidth.
It also involves opting for extra security equipment in case of any disaster or bottlenecks. Utilities like firewalls, disaster recovery plans, proxy servers and a proper backup solution should ensure to cope with DoS attacks.
For a successful approach, it should go through multiple layers of security to ensure protection to every constituent of CyberSecurity. Particularly involving computers, hardware systems, networks, software programs and the data which are shared among them.
Conclusion
In an organization, to accomplish an effective Cyber Security approach, the peoples, processes, computers, networks and technology of an organization either big or small should be equally responsible. If all component will complement each other then, it is very much possible to stand against the tough cyber threat and attacks.
If you are curious to learn more, then check out this complete cybersecurity course.
Shambhoo Kumar
A Tech enthusiast, full-time developer and cricketer for weekends. Founder of Unboxhow.com.
NEXTTop 5 Bug Bounty Platforms for Organizations to Improve Application Security »
PREVIOUS« How to Setup Fast Loading WordPress Sites on DigitalOcean?
SHARE
PUBLISHED BY
Shambhoo Kumar
FEBRUARY 24, 2019 7:25 PM
RELATED POST
Clickjacking Attacks: Beware of Social Network Identification
How to Protect Origin with Cloudflare Argo Tunnel?
9 Popular Web Application Injection Attack Types
RECENT POSTS
HOSTING
8 Best Managed MySQL Hosting Platform for your Application
MySQL is the most widely used open-source database engine in Linux and cloud-based platforms. Almost…
February 18, 2020
HOSTINGSTARTUP
14 Best Hosted Wiki Platform for Your Business
In today’s world, everybody expects swift access to information. And to go on accessing that,…
February 17 2020
SECURITY
9 Popular Web Application Injection Attack Types
The problem with web applications is that they are openly exposed to billions of internet…
February 11, 2020
DEVELOPMENT
A Friendly Introduction to Data Analysis in Python
Over the years, the use of python for data science has grown incredibly and keeps…
February 10, 2020
SECURITY
How to Protect Origin with Cloudflare Argo Tunnel?
Don’t let someone bypass Cloudflare protection and misuse your origin server! Cloudflare is one of…
February 9, 2020
SECURITY
Clickjacking Attacks: Beware of Social Network Identification
It’s hard to resist clicking on a free iPhone offer link. But be careful: your…
February 9, 2020
About Contact Sitemap Terms Privacy Disclosure Write for Us
All Rights ReservedView Non-AMP Version














